
Within the immense digital void, stories are told and electrons dance.
Information about politics, economy, culture, and security matters may be found in abundance on this platform.
Knowledge is power in today’s world, and open-source intelligence (OSINT) is a method that helps obtain information from sources that are accessible to the public. Journalists, detectives, researchers, and even regular people who wish to make educated decisions need to have access to open-source intelligence (OSINT). It’s a fantastic resource for learning about a wide range of global subjects.
In many respects, OSINT is the exact opposite of operational security (OPSEC), the security procedure via which companies safeguard publicly available information about themselves that, in the right hands, might expose potentially harmful facts.

a diverse range of methods, websites, applications, and more for looking for and extracting data from publicly accessible sources.
We’ll expose you to the best 14 OSINT websites and tools in this post, outlining their advantages and disadvantages and offering real-world applications. Additionally, we’ll suggest ten complimentary PDFs for additional reading on the topic.
Top 14 Tools & Websites OSINT
1. — Maltego — https://www.maltego.com
2. — SpiderFoot — https://www.spiderfoot.net
3. — Intelligence X — https://intelx.io
4. — Shodan — https://www.shodan.io
5. — Metagoofil — https://www.kali.org/tools/metagoofil
6. — Lampyre — https://lampyre.io
7. — Spokeo — https://www.spokeo.com
8. — Recon-ng — https://github.com/lanmaster53/recon-ng
9. — Mitaka — https://chrome.google.com/webstore/detail/mitaka/bfjbejmeoibbdpfdbmbacmefcbannnbg
10. — Babel Street — https://www.babelstreet.com
11. — Seon — https://seon.io
12. — Google Dork — GHDB — https://www.exploit-db.com/google-hacking-database
13. — Metasploit — https://www.metasploit.com
14. — Creepy — https://www.geocreepy.com
1 — Maltego

The Web’s Artisan Crafting tales of links, no less than a magician, through relationships & ties, It unveils truths & lies.
Specializes in unveiling connections among people, companies, domains, telephone numbers, e-mail & more….
— all of which can benefit anything from law enforcement investigations to cybersecurity threat detection.
- Pros: is a powerful tool for visualizing relationships between data points.
- Cons: requires a paid subscription for full functionality.
2. — SpiderFoot :
The Web’s Tracker, no trail too faint, no lead slacker, pursuing data’s footprint with care, revealing stories bare.
With more than 200 modules, it can be used either offensively for reconnaissance of a specific target or defensively to gather information about what a user might have exposed over the internet and how likely the threat of a security breach is.
- Pros: has a large number of modules for gathering information from various sources.
- Cons: may require some technical expertise to use effectively.
3. — Intelligence X:
Intelligence X is an OSINT tool that allows users to search for publicly available information across multiple sources. It provides advanced search capabilities and filters to help users find the information they need quickly and easily.
- Pros: provides advanced search capabilities for finding publicly available information almost everywhere online.
- Cons: requires a paid subscription for full functionality.
4. — Shodan:
The Internet’s Seer, a scout without peer, webcams, routers, & beyond, Its touch unveils what’s spawned.
Shodan is an OSINT tool that allows users to search for internet-connected devices and systems. It provides detailed information about these devices, including their location, operating system, and vulnerabilities.
- Pros: provides detailed information about internet-connected devices.
- Cons: may require some technical expertise to use effectively along registration or paid subscription to enhance results.
5. — Metagoofil:
https://www.kali.org/tools/metagoofil
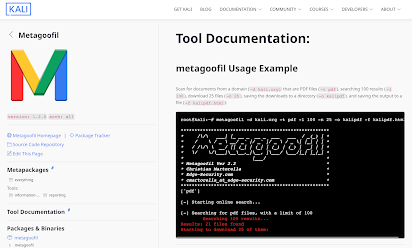
Harvester of Metadata, delving into files, it’s a crusader, extracting precious info, no task greater.
This metadata can provide valuable information about the authorship and history of these documents.
- Pros: provides detailed metadata about publicly available documents.
- Cons: may require some technical expertise to use effectively & you will need a Linux OS.
6. — Lampyre:
Lampyre is an OSINT tool that provides due diligence and cyber threat intelligence capabilities. It allows users to gather information from various sources and analyze it in order to identify potential threats or risks.
- Pros: provides advanced capabilities for due diligence and cyber threat intelligence.
- Cons: requires a paid subscription for full functionality.
7. — Spokeo:
Spokeo is an OSINT tool that allows users to search for information about US citizens, including their contact information, social media profiles, and public records.
- Pros: provides detailed information about US citizens.
- Cons: only provides information about US citizens & requires a paid subscription for full functionality.
8. — Recon-ng:
https://github.com/lanmaster53/recon-ng
Sentinel of the Web, through the vast web, its threads ebb,
It stands watch, ever keen, Unveiling what’s unseen.
It includes a wide range of modules for gathering information from various sources whilst, analyzing it to identify potential vulnerabilities or risks.
- Pros: Recon-ng is a powerful and flexible platform for conducting reconnaissance.
- Cons: Recon-ng may require some technical expertise to use effectively & a Linux OS.
9. — Mitaka:
https://chrome.google.com/webstore/detail/mitaka/bfjbejmeoibbdpfdbmbacmefcbannnbg
Available as a Chrome extension and Firefox add-on, Mitaka lets you search over six dozen search engines for IP addresses, URLs, hashes or other indicators of compromise (IoCs). It also supports VirusTotal, URLscan.io, along other popular OSINT tools.
- Pros: Mitaka is easy to use and integrates with popular web browsers.
- Cons: Mitaka may not provide as much detailed information as some other OSINT tools.
10. — Babel Street:
Babel Street is an OSINT tool that uses AI to cross language barriers for any search term. This cloud-based service allows users to search for information in multiple languages, making it easier to find relevant information from sources around the world.
- Pros: Babel Street uses AI to provide multilingual search capabilities.
- Cons: Babel Street requires a paid subscription for full functionality.
11. — Seon:
Seon is an OSINT tool that provides social and digital signal checks. It allows users to gather information from social media profiles and other online sources in order to assess the credibility of an individual or organisation.
- Pros: provides advanced capabilities for assessing the credibility of individuals or organizations based on their online presence.
- Cons: requires a paid subscription for full functionality.
12. — Google Dork / GDork / GHDB:
https://www.exploit-db.com/google-hacking-database
The Silent Whisperer, in the vast sea of Google, it dives deeper, revealing secrets, the silent keeper.
Google Dork is actually a data enquiring method that allows users to search Google using advanced operators in order to find specific information. It can be used to find sensitive information that may have been inadvertently exposed online.
- Pros: Google Dork provides advanced search capabilities using Google’s powerful search engine.
- Cons: may require some technical expertise to use effectively.
13. — Metasploit:
Metasploit is an open-source penetration testing framework that can be used as an OSINT tool. It allows users to gather information about vulnerabilities in systems and networks in order to assess their security posture.
- Pros: provides advanced capabilities for assessing the security of systems and networks.
- Cons: may require some technical expertise to use effectively & a Linux OS for better performances.
14. — Creepy:
Creepy is a geolocation OSINT tool. It allows users to gather geolocation-related information about users of social networking platforms along, with image hosting services based on their usernames or user IDs.
- Pros: provides detailed geolocation-related information about users of social networking platforms and image hosting services.
- Cons: may not provide as much detailed information about non-geolocation-related data & not currently maintained.

A story of data that freely prances instead of murmurs or glimpses that are hidden. The public’s view is so wide that its data are as unfettered as the huge sky. However, OSINT tools become heroes’ honoured callers when they go on missions of defence, study, or exploration.
They sort through the limitless, searching for uncommon catches and revealing legends and facts that were previously unknown.
Ethics is the guiding lighthouse amidst this immense ocean of data and stories.It is our responsibility to use OSINT beautifully and not as a means of obtaining loot.The OSINT anthem will always be about open truths and stories to share in this digital age where everyone is concerned in this story of data, emotion, and lore.
A few highlights about OSINT are below.
- — The first is OSINT_Handbook_2020.pdf.
OSINT Handbook 2020.pdf can be downloaded at
https://i-intelligence.eu/uploads/public-documents/OSINT_Handbook_2020.pdf
- — Open-source information is intelligence collected from publicly available sources.
https://github.com/jivoi/awesome-osint
Conclusion
In conclusion, you can obtain information from a variety of public data sources with the use of a number of potent OSINT techniques. Every tool has advantages and disadvantages, therefore it’s critical to select the best one for your particular requirements.
Note -: Legal Implications of Practicing OSINT Without Permission under Indian Law
Dear Learners,
We would like to bring to your attention an important matter concerning the practice of Open Source Intelligence (OSINT) within the context of Indian law.
While OSINT is a valuable skillset used for information gathering, it’s crucial to emphasize that engaging in OSINT activities without the explicit permission of the subject may have legal consequences. The Indian legal framework, including but not limited to the Information Technology Act, 2000, recognizes the importance of privacy and protection of personal information.
Unauthorized access to someone’s personal data, online presence, or any other form of information, even if publicly available, may lead to legal repercussions. It’s essential to respect individuals’ privacy and adhere to ethical standards when conducting OSINT activities.
As a responsible community, we encourage all members to be aware of and comply with relevant laws and regulations. If you have any doubts or concerns about the legality of specific OSINT practices, it is advisable to seek legal advice to ensure compliance with Indian laws.
Let’s build a community that values ethical conduct and respects the rights and privacy of individuals. Thank you for your understanding and cooperation in this matter.
If you have any questions or need clarification, please feel free to reach out to us.
Best regards,
Somya Gupta
Defronix
Please feel free to ask any questions or make any comments below. I appreciate you reading!

