TOR (The Onion Router):
1. Overview:
TOR, or The Onion Router, is a widely-used anonymity network that allows users to access the internet with enhanced privacy. It operates by routing traffic through a series of volunteer-operated servers, encrypting the data in layers like an onion. This makes it difficult to trace the origin and destination of the communication, providing a degree of anonymity for users.
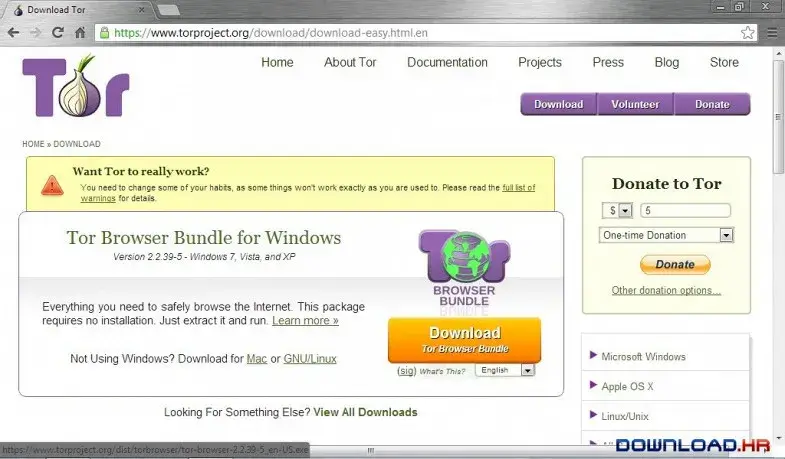
2. Accessibility:
TOR is known for its accessibility. Users can download the TOR Browser, a modified version of Firefox, to easily access the TOR network and browse the internet anonymously. The network is designed to protect users from traffic analysis, censorship, and surveillance.
3. Speed:
One drawback of TOR is that its onion routing process can result in slower speeds compared to regular internet browsing. The data passing through multiple nodes in the network introduces latency, affecting the overall user experience.
4. Use Case:
TOR is primarily used for anonymous browsing and accessing regular websites on the internet. It has become a vital tool for individuals seeking privacy and security, especially in regions with restricted internet access.
I2P (Invisible Internet Project):
1. Overview:
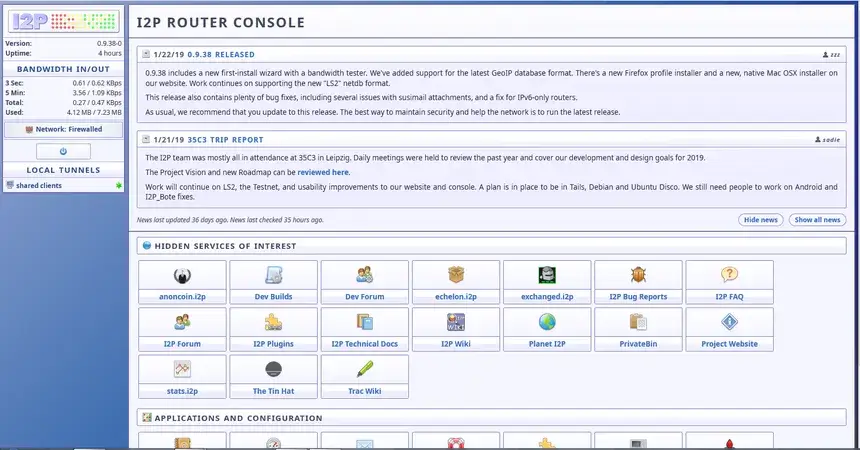
I2P, or the Invisible Internet Project, is a decentralized network that focuses on providing anonymous communication and file sharing within its network. Unlike TOR, I2P aims to create a fully decentralized environment where all nodes are equal, enhancing resilience against attacks and censorship.
2. Decentralization:
I2P’s architecture is built on decentralization. It uses a distributed, peer-to-peer model, and all nodes in the network contribute to the routing of traffic. This decentralized approach contributes to the robustness and censorship resistance of the network.
3. Speed:
I2P is designed to provide faster and more efficient anonymous communication within its network. The focus is on creating a secure and private environment for users to communicate and share files without relying on centralized servers.
4. Use Case:
I2P is tailored for anonymous communication within the I2P network itself. Users can send messages, share files, and engage in various activities within the decentralized I2P ecosystem. It’s particularly suitable for those who prioritize decentralized, peer-to-peer communication.
Conclusion:
The choice between TOR and I2P depends on the specific privacy needs and use cases of the individual. While TOR is more accessible and widely used for anonymous internet browsing, I2P offers a decentralized environment with a focus on anonymous communication within its network. Users should carefully consider their requirements and the strengths of each network before choosing the one that aligns with their privacy goals.